Most people connected to the Internet have heard of the term “malware”, but not many have heard of “ransomware”. Malware can be defined as any software designed to harm or destroy a computer system. Viruses, Trojans, worms, spyware and adware are types of malware. Ransomware is malicious software that is designed to infiltrate a computer system and alter data in a manner that makes the data inaccessible – typically by use of encryption. In order to decrypt your files, you must obtain a decryption key. Access to the decryption key is held by the attacker until their ransom demands are met. This type of attack is considered low risk, requires little skill, and has the potential for a high payout which is why the popularity of ransomware is on the rise.
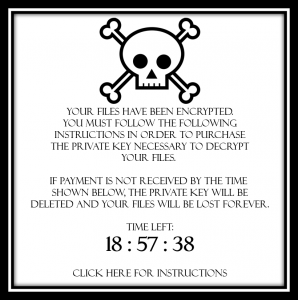
As you read this article, keep this question in the back of your mind, “How much is my data worth to me?” Consider this scenario. You sit down at your computer and move your mouse to awaken your sleeping monitor. At first you are confused because the desktop picture of your favorite cat meme has been replaced by a webpage displaying the following information:
The instructions detail how to initiate the payment process as well as the amount and currency in which the payment must be made. For anonymity purposes, the ransom will likely be demanded in bitcoin, an online currency that will be discussed in a future article. The ransom could range anywhere from several hundred dollars to several million dollars, and depending on the variant of ransomware, your decryption key may be automatically deleted if any attempts to remove the ransomware are taken.
Once you have finished reviewing the attacker’s demands, you’ll likely think it is a mean and elaborate prank that one of your friends or coworkers is playing on you. However, soon you will realize that this is anything but a prank and you’ll immediately begin thinking about your most valuable files. Wedding pictures, pictures of your baby, work projects, school projects, tax documents, etc. You will try to recall when you last backed up your data and crumble when you realize your last backup was almost a decade ago. As your anger turns to grief, you will realize that your only course of action is to pay the attackers whatever absurd amount of money they have demanded or lose your seemingly priceless data.
The fact of the matter is, even if you decide to pay the ransom, there is nothing preventing the attacker from asking for more money or simply deleting the decryption key after receiving payment. This turned out to be the case in a recent ransomware attack on Kansas Heart Hospital in May 2016 where hospital officials decided to pay the attackers “a small amount” to unlock their captive data. The attackers responded by asking for a second ransom which the hospital refused to pay. Medical facilities, such as hospitals, are prime targets for ransomware attacks due to the sensitive nature of the files they possess.
So how does an individual or organization prepare for such an attack? While it sounds cliché, knowledge is power. Educate yourself and/or your organization on proper information assurance practices such as not opening attachments or links from unrecognized sources. I once helped a friend with a computer problem that turned out to be caused by an infestation of malware. When I asked my friend if she knew how it happened, she said that she had no idea and that she only used the computer for writing reports for school. She later confessed that she came across a USB flash drive in the grocery store parking lot which she plugged into her computer and attempted to open some files. All I could do was sigh and say that probably wasn’t such a great idea, and while I was never able to identify the USB drive as the source of the malware (it was never in my possession), it very well could have been and it is a shining example of what not to do when you come across random storage devices.
In addition to educating on proper data-handling techniques, I also recommend you follow the four rules of data management:
- Backup your data
- Backup your data
- Backup your data
- Backup your data
Backing up your data, alone, will do little to prevent ransomware attacks; however, by doing so, you remove the attacker’s power should their attack be successful. Taking it a step further, you might also consider backing up your data to multiple (detached) locations or having backups of your backups. Backup tools and techniques will also be discussed in a future article.
The reason why ransomware is such a threat is because the attack does not need to be aimed at a Fortune 500 company in order to be effective. Individuals, small business owners, non-profit organizations, medical facilities, schools, government entities, etc. can all be targeted by ransomware, which is why it is paramount for everyone to be aware of such cyber-threats and to know how to react in the event of a breach. In the attack on Kansas Heart Hospital, patient data was not compromised and the hospital was able to regain control of their data thanks to the policies and procedures that were in place at the time of the attack. This helped minimize the impact of the cyber-attack on their operations. Earlier in the article I asked for readers to contemplate the value of their most important files. Given the provided information, what measures will you take in order to prevent or mitigate future attacks on you or your organization?